Now some resources are slowly starting to creep into i2p, so the question has arisen about convenient access to this network.
You can install an i2p router on your computer. Who wants to provide access to their entire home network, set up a proxy on their home router.
But my question was different. I wanted to be able to access i2p from any computer without installing additional software, even at the cost of security - because I don’t need to hide, but just look at something. If it is possible to launch a remote desktop, then I prefer to connect to my home server from all Internet cafes and guests, and my configured environment is already there. In the case of a slow connection or closed ports, using RDP becomes difficult. Therefore, the simplest and most undemanding option is to install an i2p router on the hosting and set up an http proxy.

There are no special requirements here, VDS or just a rented server - depending on your needs and financial capabilities. If only there was a machine with root access that could run java. The OS is not critical, if you really want to, then you can raise a proxy on Windows. But I did it on Linux - it’s cheaper and more familiar. Hardware - AMD Athlon 64 5600+ X2, 2 GB RAM. But this is redundant; I also installed such a proxy on an inexpensive VDS with 256 RAM. True, it didn’t work very quickly and took up a decent percentage of resources.
OS - debian wheezy. The choice of distribution does not matter, I just got used to Debian over the past 15 years.
First, add the i2p repository to sources.list:
Download the repository key www.i2p2.de/_static/debian-repo.pub and add it to apt:
We update the package database and install i2p and the i2p-keyring package (repository key updates):
Dependencies (including java) will be pulled out automatically.
You can start ip2 by simply typing "i2prouter start" in the console or as a service at system startup. It’s more convenient, of course, with the service.
We are recruiting "dpkg-reconfigure i2p" (on behalf of root), when asked about starting the service, answer “Yes”. Also at this step you can set the size of the allocated memory, left 128MB and create a user to run the i2p router.
For Ubuntu, everything is configured in the same way, the command to add a repository is only different. More details here.
For other distributions you need to install java (sunjava, openjdk), download the archive from here and run the console installer "java -jar i2pinstall_ХХХХ.jar -console". Launching as a service remains at the user's discretion.
As a lazy person, I prefer web interfaces rather than configuration files. :)
Initially, access to the web interface is allowed only from the local computer. So we will make the first security hole - open access to the admin panel from any address. But first you need to somehow reach her. We take ssh and make a tunnel from port 7657 of the hosting to port 7657 of our computer.
If we see a shell invitation, then follow the link http://127.0.0.1:7657/ The admin panel of the i2p router becomes available.
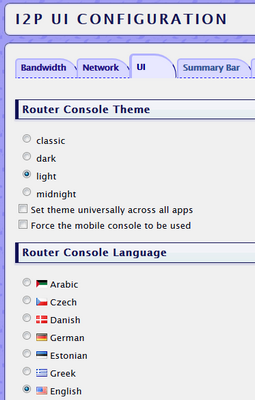
Firstly, on UI tab set the language to English. Because if you need to find something, it’s easier to search by the English names of the terms, rather than by the Russian ones. For example, you won’t immediately guess that “transit traffic” is “share bandwidth».

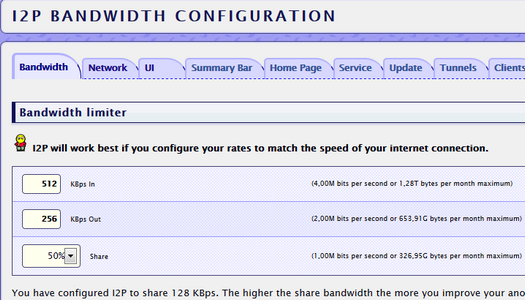
Bandwidth tab — I set IN to 512, OUT to 256 and 50% share (the same transit traffic through your server).
Hosting with traffic restrictions (even ten terabytes), but I don’t want to spend a lot on strangers, I have my own needs. Of course, anonymity and, potentially, speed suffer. I want anonymity - share 100%. Speeds must be adjusted depending on the channel of your server and your needs.

Next, set up the address book - go to http://127.0.0.1:7657/dns, there's a bookmark there Subscriptions. Initially there is only www.i2p2.i2p/hosts.txt, which is rarely updated.
Add
In general, all three are not necessary, they can overlap, but I think it won’t be worse. If you want, you can also search for lists of resources online.

We begin to add the first hole - we make access to the admin panel from any host, without tunnels
After this, the entrance to the admin panel should be available via the link http://your_server:7657, You should be prompted for a password when logging in.
By the way, for the sake of order, you can still change the port to some other one; it won’t protect you from a targeted attack, but it can protect you from randomly running bots. Although it would be better not to open access at all, but I’m a lazy person and I don’t want to open an ssh tunnel every time to enter the settings. And sometimes you have to log in to restart the service.
We open access to proxies from any IP. Of course, the correct option is to simply forward the ssh tunnel to the desired port:
And set the proxy in the browser settings 127.0.0.1:4444

But, as I said above, all this is being started not for the sake of security, but for the sake of convenience, so I’ll just open a port on the proxy.
Restart the server, wait a couple of minutes for the tunnels to rise.
If necessary, you can similarly configure an https proxy to same page.
That's right - a separate browser with scripts, flash and other silverlights disabled, in which in the settings all traffic is driven through an i2p proxy, to which an encrypted tunnel is connected (see above).
Wrong, but convenient - a script for the main browser that automatically switches proxies.
The browser configuration script is in /usr/share/doc/i2p-router/examples/scripts/i2pProxy.pac.gz
Unpack it and put it somewhere in the webserver folder (you have a webserver on your hosting? :)).
If you installed it manually from the site, then the script is in the folder script/i2pProxy.pac.
We are looking for a line in the file
We save, in the browser we go to the proxy settings in the “automatic configuration script” field we write

All. You will browse the network as usual, but when accessing i2p, the browser will automatically go through your i2p proxy, asking for a password.
The solution is simple, platform-independent and does not require installation of additional software. It should even work on Android and other iOS, if the browser there supports proxies.
But on my permanent computers, I prefer to switch access channels using the FoxyProxy plugin - I have more complex proxy selection rules than i2p/the rest of the Internet. :)
FoxyProxy for Firefox: addons.mozilla.org/en-US/firefox/addon/foxyproxy-standard
For chrome: chrome.google.com/webstore/detail/foxyproxy-standard/gcknhkkoolaabfmlnjonogaaifnjlfnp
For IE: getfoxyproxy.org/downloads/FoxyProxy-Standard-IE-1.0.8.exe (It didn't work for me in IE11).
The result is a convenient, but unsafe personal proxy for accessing the i2p network, which can be used from almost anywhere and from any OS. But for personal safety, you still need to encrypt the channel from your computer to the server - either an ssh tunnel or a vpn.
You can install an i2p router on your computer. Who wants to provide access to their entire home network, set up a proxy on their home router.
But my question was different. I wanted to be able to access i2p from any computer without installing additional software, even at the cost of security - because I don’t need to hide, but just look at something. If it is possible to launch a remote desktop, then I prefer to connect to my home server from all Internet cafes and guests, and my configured environment is already there. In the case of a slow connection or closed ports, using RDP becomes difficult. Therefore, the simplest and most undemanding option is to install an i2p router on the hosting and set up an http proxy.

Hosting
There are no special requirements here, VDS or just a rented server - depending on your needs and financial capabilities. If only there was a machine with root access that could run java. The OS is not critical, if you really want to, then you can raise a proxy on Windows. But I did it on Linux - it’s cheaper and more familiar. Hardware - AMD Athlon 64 5600+ X2, 2 GB RAM. But this is redundant; I also installed such a proxy on an inexpensive VDS with 256 RAM. True, it didn’t work very quickly and took up a decent percentage of resources.
Installing i2p
OS - debian wheezy. The choice of distribution does not matter, I just got used to Debian over the past 15 years.
First, add the i2p repository to sources.list:
deb http://deb.i2p2.no/ stable main
deb-src http://deb.i2p2.no/ stable mainDownload the repository key www.i2p2.de/_static/debian-repo.pub and add it to apt:
apt-key add debian-repo.pubWe update the package database and install i2p and the i2p-keyring package (repository key updates):
apt-get update
apt-get install i2p i2p-keyringDependencies (including java) will be pulled out automatically.
You can start ip2 by simply typing "i2prouter start" in the console or as a service at system startup. It’s more convenient, of course, with the service.
We are recruiting "dpkg-reconfigure i2p" (on behalf of root), when asked about starting the service, answer “Yes”. Also at this step you can set the size of the allocated memory, left 128MB and create a user to run the i2p router.
For Ubuntu, everything is configured in the same way, the command to add a repository is only different. More details here.
For other distributions you need to install java (sunjava, openjdk), download the archive from here and run the console installer "java -jar i2pinstall_ХХХХ.jar -console". Launching as a service remains at the user's discretion.
Basic i2p setup
As a lazy person, I prefer web interfaces rather than configuration files. :)
Initially, access to the web interface is allowed only from the local computer. So we will make the first security hole - open access to the admin panel from any address. But first you need to somehow reach her. We take ssh and make a tunnel from port 7657 of the hosting to port 7657 of our computer.
C:\>ssh user@ваш_сервер -L7657:127.0.0.1:7657
user@ваш_сервер's password:
Linux ваш_сервер 3.2.0-4-amd64 #1 SMP Debian 3.2.51-1 x86_64
You have mail.
Last login: Tue Dec 24 06:18:58 2013
ваш_сервер:~>
If we see a shell invitation, then follow the link http://127.0.0.1:7657/ The admin panel of the i2p router becomes available.
Firstly, on UI tab set the language to English. Because if you need to find something, it’s easier to search by the English names of the terms, rather than by the Russian ones. For example, you won’t immediately guess that “transit traffic” is “share bandwidth».
Bandwidth tab — I set IN to 512, OUT to 256 and 50% share (the same transit traffic through your server).
Hosting with traffic restrictions (even ten terabytes), but I don’t want to spend a lot on strangers, I have my own needs. Of course, anonymity and, potentially, speed suffer. I want anonymity - share 100%. Speeds must be adjusted depending on the channel of your server and your needs.
Next, set up the address book - go to http://127.0.0.1:7657/dns, there's a bookmark there Subscriptions. Initially there is only www.i2p2.i2p/hosts.txt, which is rarely updated.
Add
http://i2host.i2p/cgi-bin/i2hostetag
http://stats.i2p/cgi-bin/newhosts.txt
http://no.i2p/export/alive-hosts.txtIn general, all three are not necessary, they can overlap, but I think it won’t be worse. If you want, you can also search for lists of resources online.

Access to the admin panel from any computer
We begin to add the first hole - we make access to the admin panel from any host, without tunnels
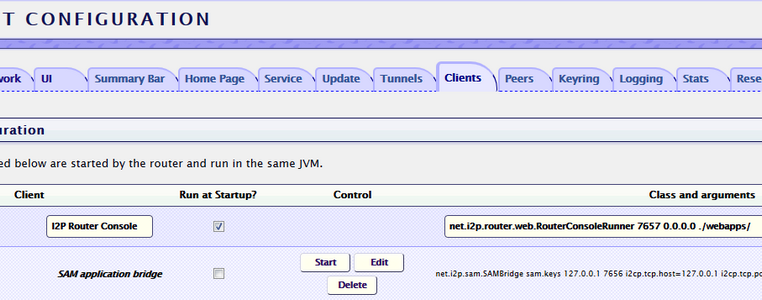
- http://127.0.0.1:7657/configclients, field "I2P Router Console", click Edit and change clientApp.0.args=7657 ::1,127.0.0.1 ./webapps/ on clientApp.0.args=7657 0.0.0.0 ./webapps/

- http://127.0.0.1:7657/configui, at the bottom, under the list of languages, fields for entering the name and password for the admin panel.

- Reboot the i2p router (for example, with the Restart button on the left).

After this, the entrance to the admin panel should be available via the link http://your_server:7657, You should be prompted for a password when logging in.
By the way, for the sake of order, you can still change the port to some other one; it won’t protect you from a targeted attack, but it can protect you from randomly running bots. Although it would be better not to open access at all, but I’m a lazy person and I don’t want to open an ssh tunnel every time to enter the settings. And sometimes you have to log in to restart the service.
Setting up an http proxy
We open access to proxies from any IP. Of course, the correct option is to simply forward the ssh tunnel to the desired port:
C:\>ssh user@ваш_сервер -L4444:127.0.0.1:4444
user@ваш_сервер's password:
Linux ваш_сервер 3.2.0-4-amd64 #1 SMP Debian 3.2.51-1 x86_64
You have mail.
Last login: Tue Dec 24 07:37:52 2013
ваш_сервер:~>
And set the proxy in the browser settings 127.0.0.1:4444

But, as I said above, all this is being started not for the sake of security, but for the sake of convenience, so I’ll just open a port on the proxy.
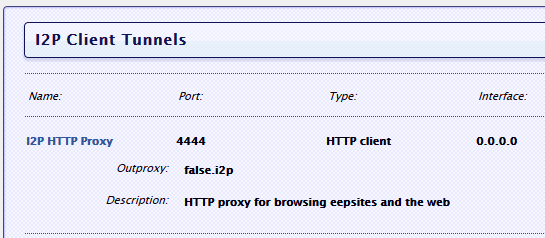
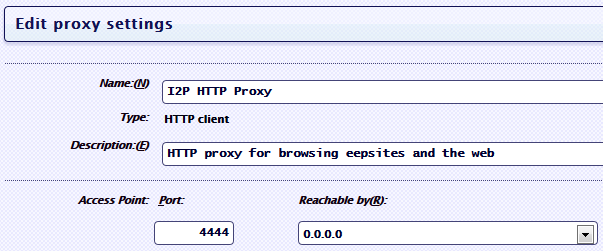
- Let's go to http://your_server:7657/i2ptunnelmgr, we are looking for a tunnel there called "I2P HTTP Proxy", go to its settings.

- In point Access Point - Reachable by choose 0.0.0.0

- Then we set a password. Field Local Authorization, check in Enable, set the name and password and click Save.

Restart the server, wait a couple of minutes for the tunnels to rise.
If necessary, you can similarly configure an https proxy to same page.
Browser settings
That's right - a separate browser with scripts, flash and other silverlights disabled, in which in the settings all traffic is driven through an i2p proxy, to which an encrypted tunnel is connected (see above).
Wrong, but convenient - a script for the main browser that automatically switches proxies.
The browser configuration script is in /usr/share/doc/i2p-router/examples/scripts/i2pProxy.pac.gz
Unpack it and put it somewhere in the webserver folder (you have a webserver on your hosting? :)).
If you installed it manually from the site, then the script is in the folder script/i2pProxy.pac.
We are looking for a line in the file
var i2pProxy = "PROXY 127.0.0.1:4444"; and change the IP address and port to yours.We save, in the browser we go to the proxy settings in the “automatic configuration script” field we write
имя_вашего_сервера/путь_к_i2pProxy.pac
All. You will browse the network as usual, but when accessing i2p, the browser will automatically go through your i2p proxy, asking for a password.
The solution is simple, platform-independent and does not require installation of additional software. It should even work on Android and other iOS, if the browser there supports proxies.
But on my permanent computers, I prefer to switch access channels using the FoxyProxy plugin - I have more complex proxy selection rules than i2p/the rest of the Internet. :)
FoxyProxy for Firefox: addons.mozilla.org/en-US/firefox/addon/foxyproxy-standard
For chrome: chrome.google.com/webstore/detail/foxyproxy-standard/gcknhkkoolaabfmlnjonogaaifnjlfnp
For IE: getfoxyproxy.org/downloads/FoxyProxy-Standard-IE-1.0.8.exe (It didn't work for me in IE11).
Conclusion
The result is a convenient, but unsafe personal proxy for accessing the i2p network, which can be used from almost anywhere and from any OS. But for personal safety, you still need to encrypt the channel from your computer to the server - either an ssh tunnel or a vpn.